Security Orchestration, Automation and Response is a hot topic indeed, as SOAR platform became a fundamental part of any security operation center today for incident response, automation and orchestration to allow incident response teams to act faster and smarter.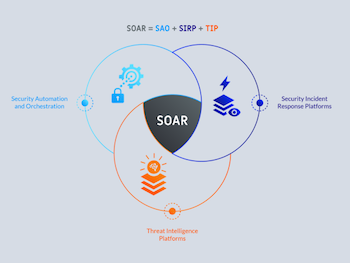
In this article we will focus on what's SOAR, what's the value behind it and how to implement it in your operation and it's the first in a series of articles about SOAR, its evolution, best practice for SOAR and who would be really using SOAR and gaining benefit from having it in their operations.
Back in 2017, when SOAR technologies started to gain great momentum, and Gartner released it's first market review for SOAR technologies, it was indeed a very special times not only because of the great value orchestration and automation can introduce to enterprises and MSSPs, but also due to the initial confusion that created in the market at that time :)
Gartner guidelines introduced SOAR as SIRP + SOA and TIP, and it was really interesting due to the confusion among organizations and even vendors at that time .. I can't help myself linking my 4 years' kid - Adam - games and cartoons to what was happening, it was like the popular toddlers' question game to discover new stuff and the game this time is WHAT's SOAR? :))
IS IT an Automation Workflow?! Adam screaming .. NOOO
IS IT Ticketing System? NOOOO
IS IT Threat Intelligence Platform? NOOO
IS IT SIRP?? NOOOO
IS IT all of that?? MAYBE .. MAYBE NOT :)) - Adam answers with frustration and he started to get bored from the interesting game and the value behind.
It was that interesting because everyone was trying to align to Gartner's report as it drives discussions with enterprises and business and simply most of the vendors started to position themselves as SOAR marketing-wise (as it usually happen) regardless of what they actually do and which category of products' they fall in.
So, let's discover the YES answer for the above questions together :) and to understand what's really SOAR let's look first at SOAR evolution ..
Back at 2010, when an analyst faces a case, he used to depend on some excel sheets for best practices and his own skills, if he didn't get his coffee in the morning or not feeling well at that day .. you cannot for sure expect the outcome. :)
As a result, there was a need to use a ticketing system for the analyst to organize his work and his interaction with the other teams across the organization .. hence the use of corporate Ticketing systems started in security operation centers ..
Then quickly the enterprises and the market realized due to the nature of sensitive information and confidentiality that part of the security incidents they cannot depend on the corporate ticketing system and they must have their own ticketing system in the security operation center, still they needed to link and integrate the two systems -- the corporate ticketing system and the security ticketing system) for assigning tasking and manage interactions with other teams in the organization ..
Then .. again the market realized that ticketing system are not security purpose-built ticketing system! it lacks many security features and functionalities that needed in day to day operations ..
So by 2013, the first Security Incident Response Platform got created -- GUESS WHICH VENDOR ;) -- and basically it was a ticketing system with the security features and functionalities needed like NIST and SANS playbooks included, utilizing threat intelligence, incident visualizaton, automatic assignment, SLA management ..etc
and the market was like -- YESSS we got it .. we have the tasks and step by step guidance for each incident according to its type .. SO LET's DO IT .. LET's AUTOMATE IT :)
and great hype about AUTOMATION started to kick in .. BUT with BIG FAILURE ..
Want to know why? that's we gonna go through in the next part of this article ;) STAY TUNED ..